The Strategic Rationale for Outsourcing Cybersecurity
Faced with an overwhelming threat landscape and an untenable skills gap, savvy business leaders are reframing their approach to cybersecurity. They are moving away from viewing it as a sunk cost or an operational burden and toward recognizing it as a strategic investment in business resilience and a key enabler of growth. Strategic outsourcing emerges as the most logical and effective solution to this conundrum.
Compounding the threat landscape is a critical and worsening global shortage of qualified cybersecurity professionals. The (ISC)² Cybersecurity Workforce Study, a leading benchmark report, consistently reveals a multi-million person gap between the demand for skilled cybersecurity workers and the available supply. For small and medium-sized businesses (SMBs) in the US, this is not an abstract statistic; it is a harsh operational reality. They find themselves in a fiercely competitive market, unable to match the salaries, benefits, and career progression opportunities offered by large enterprises and technology giants.
Consequently, many businesses are forced to rely on generalist IT teams who, despite their best efforts, lack the specialized skills in areas like threat hunting, incident response, security analytics, or penetration testing. They cannot realistically provide the 24/7/365 monitoring required to detect and respond to threats in real-time. This talent scarcity makes building an effective, in-house security operations team a financial and logistical impossibility for a vast majority of US businesses, creating a dangerous vulnerability that adversaries are all too eager to exploit.

The nature of cyber threats has evolved with breathtaking speed, moving far beyond the simple viruses and malware of decades past. Today's adversaries are organized, well-funded, and ruthlessly efficient, employing a diverse arsenal of attack vectors. Ransomware attacks, as meticulously detailed in reports from cybersecurity firms like Mandiant and CrowdStrike, have morphed into multi-faceted extortion schemes involving data exfiltration and public shaming, capable of paralyzing an entire organization for weeks. Business Email Compromise (BEC) and sophisticated phishing campaigns continue to exploit the human element, resulting in billions of dollars in direct financial losses annually, a fact consistently highlighted in the FBI's Internet Crime Complaint Center (IC3) reports.
Beyond these, businesses face Advanced Persistent Threats (APTs), often state-sponsored groups that infiltrate networks for long-term espionage or disruption, and insidious supply chain attacks, where adversaries compromise a trusted vendor to gain access to their downstream customers. This complex and dynamic threat matrix means that a reactive, perimeter-based defense is dangerously obsolete. Effective security now demands a proactive, intelligence-driven, and multi-layered approach that is incredibly resource-intensive to build and maintain internally.
The Staggering Economic and Reputational Cost of a Breach
The consequences of a successful cyber-attack extend far beyond immediate financial loss. The IBM Security "Cost of a Data Breach Report" provides a sobering annual analysis of these impacts. The 2024 report, for instance, highlights that the global average cost of a data breach has reached new heights, with the United States consistently recording the highest average costs of any country. These figures encompass not only the direct costs of remediation, regulatory fines (under frameworks like GDPR, CCPA, and HIPAA), and legal fees, but also the more insidious and long-lasting costs of business disruption, lost revenue, and profound reputational damage. The Verizon "Data Breach Investigations Report" (DBIR) further enriches this picture by analyzing tens of thousands of real-world incidents, offering invaluable insights into which attack patterns are most prevalent in specific industries. For a business owner, the key takeaway is stark: the cost of a single major breach can be an existential threat, far outweighing the perceived cost of robust security investments.

Strategic Advantages of Outsourcing Cybersecurity: Beyond Simple Cost Savings
While cost efficiency is a significant motivator, the true value of outsourcing cybersecurity lies in the strategic capabilities it unlocks for a business. These advantages collectively transform a company's security posture from a state of vulnerability to one of strength and resilience.
- Immediate Access to Elite Talent and Specialized Expertise: Instead of spending months trying to recruit a single analyst, outsourcing instantly provides access to an entire team of certified professionals with diverse and deep expertise in areas like cloud security, threat intelligence, malware analysis, and digital forensics.
- Achieving 24/7/365 Coverage and "Eyes on Glass": The single most impactful advantage is the shift to continuous, around-the-clock monitoring. This ensures that threats are detected and responded to in minutes, not hours or days, dramatically reducing the potential for damage.
- Significant Cost Efficiencies and Predictable Operational Expenditures (OpEx vs. CapEx): Outsourcing converts the unpredictable and high capital expenditure (CapEx) of building an in-house SOC (salaries, technology, facilities) into a predictable, monthly operational expenditure (OpEx). This model often results in a lower Total Cost of Ownership (TCO) and simplifies budgeting.
- Access to Enterprise-Grade Security Technology and Platforms: Leading MSSPs and MDR providers have multi-million dollar technology stacks, including advanced SIEM, SOAR, EDR, and threat intelligence platforms. Outsourcing provides access to this powerful toolkit for a fraction of the cost of licensing and managing it directly.
- Improved Threat Detection and Faster Response Times: With specialized analysts, advanced technology, and refined processes, outsourced providers can detect threats more accurately and respond more quickly than a generalist in-house team. Key metrics like Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) are drastically improved.
- Enhanced Compliance Posture and Simplified Audits: Partnering with a provider that has expertise in frameworks like SOC 2, ISO 27001, HIPAA, or CMMC can significantly streamline the path to compliance and make audit cycles much smoother and less resource-intensive.
- Enabling In-House IT Teams to Focus on Strategic Initiatives: By offloading the demanding, 24/7 burden of security operations, in-house IT teams are freed up to focus on projects that drive business growth, such as digital transformation, improving user productivity, and deploying new applications.
It is also important to understand exactly what their role is versus yours during a crisis. Who is responsible for containment? Who communicates with stakeholders? This must be crystal clear. Look for a provider who acts as a strategic advisor and an extension of your team, not just a ticket-taking vendor. They should be proactive, transparent, and invested in your security success. Your contract should be reviewed by legal counsel and must clearly address data ownership, confidentiality, liability limits, indemnification, and a clear process for disengagement and data handover. Ensure the provider can support your growth, whether it's expanding into the cloud, adding new office locations, or accommodating increased data volume. Speak to current clients, especially those in your industry or of a similar size. A reputable provider will have a strong track record and positive references.
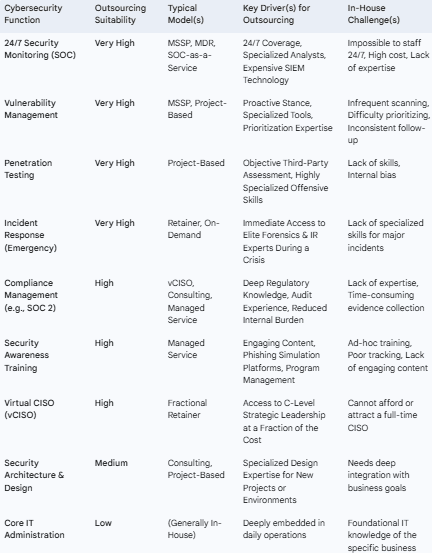


By partnering with a specialized cybersecurity provider—such as a Managed Security Service Provider (MSSP), a Managed Detection and Response (MDR) firm, or a compliance expert—businesses can instantly bridge the talent gap, gain access to enterprise-grade technology, and achieve a mature security posture far more quickly and cost-effectively than would ever be possible in-house. This allows the business to confidently pursue digital transformation, expand into new markets, and build customer trust, knowing that its digital assets are being protected by a dedicated team of world-class experts. This guide will explore precisely which roles and processes are most effectively outsourced and, crucially, the specific operational aspects a business owner must scrutinize to ensure this strategic partnership is truly effective. For US businesses ready to explore this path, platforms like Bpohub provide a vital service by connecting them with vetted, high-quality cybersecurity partners, simplifying a complex but essential journey.
